TL;DR: Make sure your GitHub organization is secure by checking that your org’s users have a sufficiently large key bittages and types (including elliptic) using this tool I wrote.
It wasn’t long ago that Ben Cox’s fantastic blog post revealed the potential threats from weak SSH keys installed on GitHub user profiles (and GitHub now disallows the installation of keys with <1024 bits). While 1024 bits is secure for now, it’s never been the tendency of the software industry to sit on its security laurels. 2048 or even 4096 bit RSA and DSA keys are now commonplace and becoming the norm, and elliptic curve keys are slowly but surely gaining traction as the industry continues to break the bad habit of assuming anything is uncrackable.
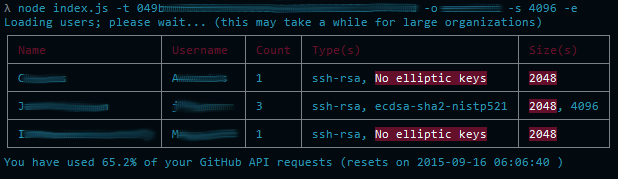
With this in mind, just how futureproof is your GitHub organization? Do you want to ensure that users are using only 2048 bit keys or larger? Do you want to find users who don’t use any keys, making commonly-typed credentials ripe for theft? Maybe security is your utmost concern, and all users should be using new ECDSA keys? With SSHaudit, you can quickly and easily determine who is and isn’t in compliance.
This utility audits public key type, number, and strength within GitHub organizations, allowing organization administrators to easily determine users which should increase the keysize of their key in order to uphold repo security.
The tool is a node.js utility written in pure JavaScript, meaning no bulky binary dependencies – just install and run!
Download now from on GitHub (MIT licensed).